
VenomServers is now moving into DDOS Protection, Our protection provides protection of 10Gbps+ and Almost all Attack Methods!
Information on DDOS Protection
Our DDOS protection works as a tunnel. we provide you with a domain such as, example.venomservers.net, this would be linked to our servers which are DDOS Protected with 10Gbps DDOS Protection each server. In the case of a downage (in case of a power outage or any other problem) another server will take the place immediately. Which would also have 10Gbps protection and Layer 4 & Layer 7 protection.
Our Server works with not only Hardware and network level protection but we also have software ddos protection. (We are in the progress of developing another program for ddos protection).We also have different packages varying on your needs. (you can contact me for a custom quote).
How does a DDoS attack occur?
A typical DDoS attack is generated from a herd of malware-infected computers that are controlled by a single operator. This herd is also known as a botnet. When a computer becomes infected by such malware, it becomes a zombie. The botnet operator has complete control of all the zombie infected computers. These herds of zombies are used to launch DDoS attacks against slave websites by flooding them with illegitimate traffic using one of many different attack methods. A botnet can contain anywhere from thousands of infected hosts to even millions.
As mentioned before, a DDoS attack can come in many forms. Botnets are capable of launching various types of DDoS attacks including: ICMP, UDP, TCP, HTTP GET/POST, SYN, and many more. VenomServers DDOS Protection provides DDoS protection against all types of attacks up to 10 Gbps, with the ability to add additional protection capacity if necessary. A typical DDoS attack will almost certainly cause downtime on an unprotected network. This will not happen at VenomServers DDOS Protection.
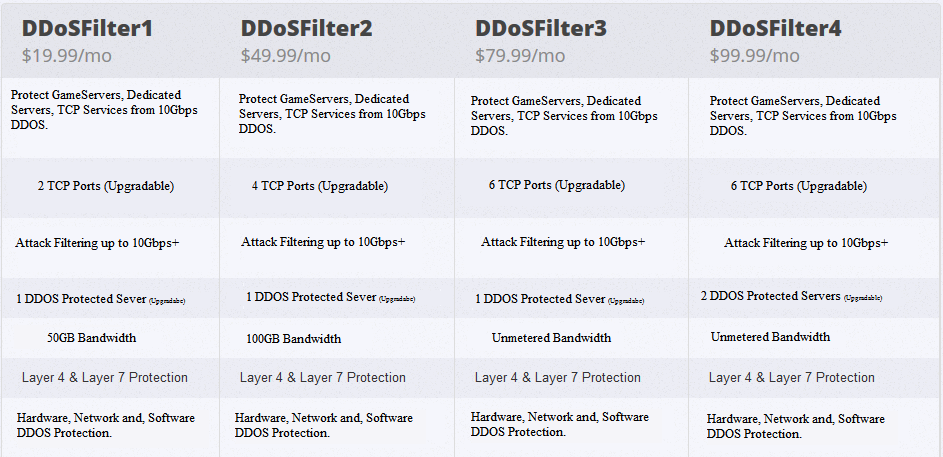
[align=center]Prices
Information on DDOS Protection
Our DDOS protection works as a tunnel. we provide you with a domain such as, example.venomservers.net, this would be linked to our servers which are DDOS Protected with 10Gbps DDOS Protection each server. In the case of a downage (in case of a power outage or any other problem) another server will take the place immediately. Which would also have 10Gbps protection and Layer 4 & Layer 7 protection.
Our Server works with not only Hardware and network level protection but we also have software ddos protection. (We are in the progress of developing another program for ddos protection).We also have different packages varying on your needs. (you can contact me for a custom quote).
How does a DDoS attack occur?
A typical DDoS attack is generated from a herd of malware-infected computers that are controlled by a single operator. This herd is also known as a botnet. When a computer becomes infected by such malware, it becomes a zombie. The botnet operator has complete control of all the zombie infected computers. These herds of zombies are used to launch DDoS attacks against slave websites by flooding them with illegitimate traffic using one of many different attack methods. A botnet can contain anywhere from thousands of infected hosts to even millions.
As mentioned before, a DDoS attack can come in many forms. Botnets are capable of launching various types of DDoS attacks including: ICMP, UDP, TCP, HTTP GET/POST, SYN, and many more. VenomServers DDOS Protection provides DDoS protection against all types of attacks up to 10 Gbps, with the ability to add additional protection capacity if necessary. A typical DDoS attack will almost certainly cause downtime on an unprotected network. This will not happen at VenomServers DDOS Protection.
Attack Types and Explained
HTTP GET Flood
An HTTP GET Flood is a Layer 7 application layer DDoS attack method in which attackers send a huge flood of requests to the server to overwhelm its resources. As a result, the server cannot respond to legitimate requests from users.
HTTPS POST Flood
An HTTPS POST Flood is an HTTP POST Flood sent over an SSL session. Due to the use of SSL it is necessary to decrypt this request in order to inspect it.
ICMP Flood
An ICMP flood is a Layer 3 infrastructure DDoS attack method that uses ICMP messages to overload the targeted network’s bandwidth.
Layer 3 and Layer 4 DDoS Attacks
Layer 3 and Layer 4 DDoS attacks are types of volumetric DDoS attacks on a network infrastructure. Layer 3 (network layer) and 4 (transport layer) DDoS attacks rely on extremely high volumes (floods) of data to slow down web server performance, consume bandwidth and eventually degrade access for legitimate users. These attack types typically include ICMP, SYN, and UDP floods.
Layer 7 DDoS Attack
A Layer 7 DDoS attack is an attack structured to overload specific elements of an application server infrastructure. Layer 7 attacks are especially complex, stealthy, and difficult to detect because they resemble legitimate website traffic. Even simple Layer 7 attacks – for example those targeting login pages with random user IDs and passwords, or repetitive random searches on dynamic websites – can critically overload CPUs and databases. Also, DDoS attackers can randomize or repeatedly change the signatures of a Layer 7 attack, making it more difficult to detect and mitigate.
SYN Flood
A SYN flood is a Layer 4 infrastructure DDoS attack method in which attackers send a huge flood of TCP/SYN packets, often with a forged sender address to the server. SYN floods bring down a network connection by using up the number of available connections the server can accept. Consequently, it becomes impossible for the server to respond to legitimate connection requests during this type of DDoS denial of service attack.
UDP Flood
UDP floods are used frequently for larger bandwidth DDoS attacks because they are connectionless and it is easy to generate protocol 17 (UDP) messages from many different scripting and compiled languages.
DNS Flood
DNS floods are used for attacking both the infrastructure and a DNS application. This denial of service attack type allows DDoS attackers to use both reflection and spoofed direct attacks that can overwhelm a target’s infrastructure by consuming all available network bandwidth.
Botnet
A botnet is a network of bots that can be commanded as a single group entity by a command and control system. Botnets receive instructions from command and control systems to launch DDoS attacks.
Booter Shell Scripts
Booter shell scripts are customizable scripts that randomize attack signatures and make attacks more difficult to differentiate from legitimate traffic. These are standalone files that execute GET/POST floods when accessed via HTTP. With booter shells, DDoS attacks can be launched more readily and can cause more damage, with far fewer machines. The skill level required to take over a web server and convert it to a bot is greatly reduced when using a booter shell. A DDoS booter shell script can be easily deployed by anyone who purchases hosted server resources or makes use of simple web application vulnerabilities such as RFI, LFI, SQLi and WebDAV exploits.
Amplification Attack
Amplification is when an attacker makes a request that generates a larger response. Examples of common amplification attacks include DNS requests for large TXT records and HTTP GET requests for large image files.
Bot
A bot is a computer that is under control of a third party.
HTTP GET Flood
An HTTP GET Flood is a Layer 7 application layer DDoS attack method in which attackers send a huge flood of requests to the server to overwhelm its resources. As a result, the server cannot respond to legitimate requests from users.
HTTPS POST Flood
An HTTPS POST Flood is an HTTP POST Flood sent over an SSL session. Due to the use of SSL it is necessary to decrypt this request in order to inspect it.
ICMP Flood
An ICMP flood is a Layer 3 infrastructure DDoS attack method that uses ICMP messages to overload the targeted network’s bandwidth.
Layer 3 and Layer 4 DDoS Attacks
Layer 3 and Layer 4 DDoS attacks are types of volumetric DDoS attacks on a network infrastructure. Layer 3 (network layer) and 4 (transport layer) DDoS attacks rely on extremely high volumes (floods) of data to slow down web server performance, consume bandwidth and eventually degrade access for legitimate users. These attack types typically include ICMP, SYN, and UDP floods.
Layer 7 DDoS Attack
A Layer 7 DDoS attack is an attack structured to overload specific elements of an application server infrastructure. Layer 7 attacks are especially complex, stealthy, and difficult to detect because they resemble legitimate website traffic. Even simple Layer 7 attacks – for example those targeting login pages with random user IDs and passwords, or repetitive random searches on dynamic websites – can critically overload CPUs and databases. Also, DDoS attackers can randomize or repeatedly change the signatures of a Layer 7 attack, making it more difficult to detect and mitigate.
SYN Flood
A SYN flood is a Layer 4 infrastructure DDoS attack method in which attackers send a huge flood of TCP/SYN packets, often with a forged sender address to the server. SYN floods bring down a network connection by using up the number of available connections the server can accept. Consequently, it becomes impossible for the server to respond to legitimate connection requests during this type of DDoS denial of service attack.
UDP Flood
UDP floods are used frequently for larger bandwidth DDoS attacks because they are connectionless and it is easy to generate protocol 17 (UDP) messages from many different scripting and compiled languages.
DNS Flood
DNS floods are used for attacking both the infrastructure and a DNS application. This denial of service attack type allows DDoS attackers to use both reflection and spoofed direct attacks that can overwhelm a target’s infrastructure by consuming all available network bandwidth.
Botnet
A botnet is a network of bots that can be commanded as a single group entity by a command and control system. Botnets receive instructions from command and control systems to launch DDoS attacks.
Booter Shell Scripts
Booter shell scripts are customizable scripts that randomize attack signatures and make attacks more difficult to differentiate from legitimate traffic. These are standalone files that execute GET/POST floods when accessed via HTTP. With booter shells, DDoS attacks can be launched more readily and can cause more damage, with far fewer machines. The skill level required to take over a web server and convert it to a bot is greatly reduced when using a booter shell. A DDoS booter shell script can be easily deployed by anyone who purchases hosted server resources or makes use of simple web application vulnerabilities such as RFI, LFI, SQLi and WebDAV exploits.
Amplification Attack
Amplification is when an attacker makes a request that generates a larger response. Examples of common amplification attacks include DNS requests for large TXT records and HTTP GET requests for large image files.
Bot
A bot is a computer that is under control of a third party.
[align=center]Prices
Terms Of Services
url: http://venomservers.net
Follow us for more info!
https://www.facebook.com/pages/Venomservers/523319094382033
https://twitter.com/VenomServersNet



